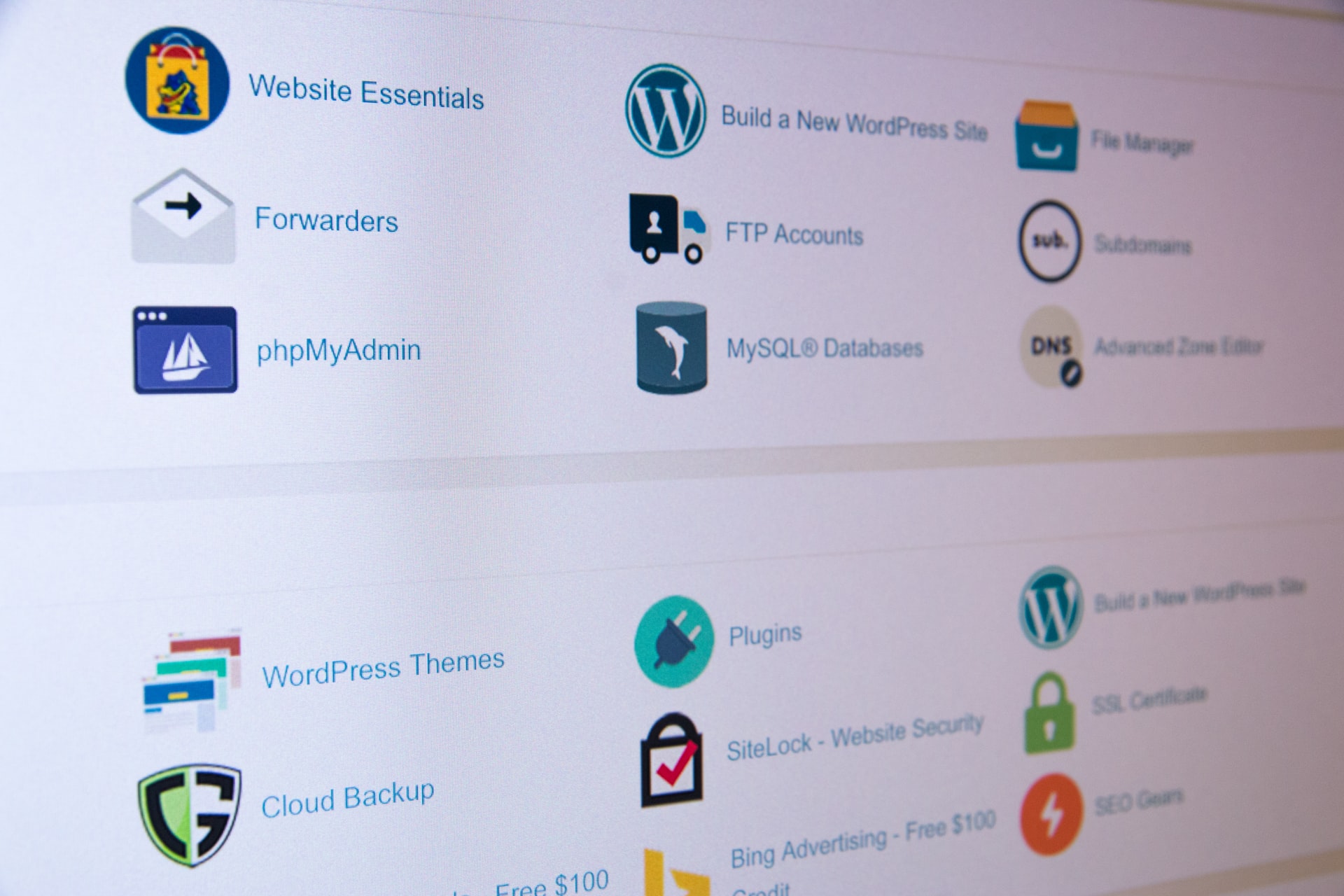
For any business dealing with customers online, security protocals are a must. You can have the most loyal customers in the world, but their patience will be brought to a test as soon as something goes wrong — and you may learn that your user base is not as forgiving as you have hoped.
Customers are expecting secure means of ordering products and services, and rightfully so. Furthermore, with network downtime costing over $300,000 per hour, according to Gartner, any security malfunction can cause serious financial, operational and reputational harm to a business.
All of this can be avoided through effective security measures that instill confidence in your users and protect your business from both malevolent and unintentional damages.
What Are SSL Certificates and How Do They Work?
The TLS/SSL certificates are cryptographic protocols used to encrypt data being exchanged between a business and a user’s browser, and to authenticate the identity of the business’s website. To clarify, TLS and SSL are often used interchangeably, with TLS (Transport Layer Security) being an improved version of SSL (Secure Socket Layers).
When a user wishes to access a website through a browser or through a smart device, the TLS protocol checks the server’s public key to confirm its identity. For a user, this provides certainty that the website is safe to use and does indeed represent the business it claims to.
The most often use of the TLS protocol is on the HTTPS (Hyper Text Transfer Protocol Secure) websites that show in the browser with a grey padlock. That symbol confirms that the website is secured by a TLS/SSL certificate. Users can get more details about the certificate and the website itself by clicking on the padlock, to provide transparency and ease of mind.
If the website has no security protocol in place, or if it does but the certificate has expired, when logging onto the website the user will be warned that the server is not secure. Some users will be allowed to override the warning and visit the website anyway, but users protected by firewall will be prevented from doing so. Either way, it makes the user question the business’s validity and reputation when they receive this kind of warning.
PKI Certificate Management
Public Key Infrastructure or PKI is another online security framework put in place to protect the communication between the server and the user. PKI uses three different components to verify that the user is who they claim to be, as well as to encrypt the reply they receive from the website.
These three components are Digital Certificates, Certificate Authority, and Registration Authority. They are crucial to secure digital communication and transactions by providing end-to-end encryption. Certificate Authority associates public keys to user identities and makes this data permanently stored. Registration Authority is a component of the Certificate Authority used to sign email messages and the like.
How Can Security Framework Protect Your Business?
There are many moving parts to successfully managing an online business, but gaining user’s trust and maintaining it is a big aspect of e-commerce, or any other website that has two-way communication with its users. The TLS/SSL and PKI security standards provide a piece of mind for both the customer and for the business itself. The security certificates ensure that the users’ data won’t end up in wrong hands and that the website will remain immune to costly security breaches.
To ensure your website’s security, your organization needs to manage the TLS/SSL certificates in a streamlined, efficient manner that prevents unexpected downtime and security breaches. With so many things that can go wrong, from an expired certificate to vulnerable cryptographic keys, by partnering up with an experienced online security expert offering a one-platform solution for all of your technology security measures, you can rest assured that your data is as protected as it can be.